The “Open Sesame” of the Digital Age
It isn’t just about keeping burglars out, but about precisely defining who may access which areas when.
The key benefits
Comprehensive efficiency advantages through complete systems
Time savings for security, human resources and IT
High-tech components in every building
Employees, suppliers, visitors... people in a wide variety of roles can occur at every organization and facility. A networked access control system defines which doors open for each of them - and much more besides.
Whether it’s a small physician’s practice, a research institute or a large manufacturing enterprise, it’s always important to protect equipment and documents, information and business processes. While the boss can go wherever he or she pleases, it can make sense to keep secretaries out of a factory hall or block assembly workers from entering the accounting department. Visitors, suppliers and service providers also need to be considered ― like when a cleaner works in the administration building every other workday between 6 and 8 p.m. or a supplier drops off merchandise during the night.
A lock and key aren’t enough for managing such a wide range of requirements; keys can be lost or stolen, among other reasons.
The answer is a professional access control system with RFID (radio frequency identification) technology. This involves providing company ID cards, badges or key fobs with tiny integrated chips able to receive and transmit radio signals. Authorizations to enter certain areas (or not) can then be centrally controlled.

“State-of-the-art access control systems are designed to perform multiple tasks, such as access control, time management, and enabling and disabling intrusion alarm systems.”
By putting an end to the need to key in the same information two or more times and concurrently manage multiple solutions, a solution of this kind greatly boosts efficiency and reliability.
“Time management in particular poses increasingly complex challenges in today’s working world,” Thomas Christian adds. “The current trend is toward flexible working hours. Companies need solutions that are able to capture time worked on a wide range of devices, also offsite.”
High-tech components in every building
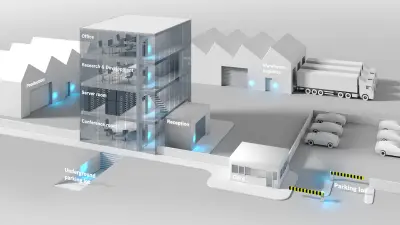
The benefits that an integrated system of this type can deliver are illustrated by a manufacturing company that uses the MATRIX solution from Bosch.
All of its buildings are equipped with appropriate components for flexibly controlling which persons may enter individual areas. Access to the main administration building is regulated by online readers with door monitors, while internal doors are protected by digital cylinders and electronic locks. Depending on how each employee’s or visitor’s ID is configured, certain doors either open or remain locked.
It’s especially important to restrict access to highly sensitive areas such as R&D labs or server rooms, so their doors are protected by biometric authentication with hand vein scanners.
The production hall, the warehouse and the loading and unloading areas are also guarded by access readers. The underground garage is safeguarded by long-range readers that detect transponders in approaching vehicles at a distance of between five and eight meters and open the door for them so they can drive right in without having to brake.
An intelligent gate also automatically controls visitor and delivery traffic to ease the workload of staff.
The access control system is linked to a higher-level management system and the human resources system. Authorized staff can use their company ID card to activate and deactivate the access control system. All threads run together in the software, which ensures absolutely smooth coordination of all networked functions.
This Bosch solution from a single source offers many advantages
One major advantage of a complete solution of this kind is that it makes work easier ― and not only for the security manager, but also for many other employees and departments. A sophisticated system of roles is used to determine who receives which information. For the personnel department, for example, information from the time clock system such as attendance, missed days and overtime is relevant. It can be evaluated at the press of a button and automatically flows into the wage and salary program. Company-specific requirements and standard contracts are also easy to implement in this way.
“Each company has different processes and high-security areas, and therefore requires its own custom-tailored access control system,” stresses Thomas Christian. “It’s also important for the solution to be scalable so it can grow with the enterprise.” It’s simplest when not only the equipment itself but also all associated services ― from consulting and planning across proper installation and commissioning all the way to maintenance and repairs ― comes from one and the same source. This way, you get a completely compatible, consistent solution and there is a single partner to turn to for getting all of your needs met.
The first step is to analyze the risks. The client is informed about potential threats to staff and facilities, and then different security areas are defined. Not only internal processes, but also the special features of each building and any preexisting security equipment are taken into account. This results in a customized security concept that minimizes costs and effort for the client. To ensure first-rate technical quality down to the tiniest detail while complying with all applicable standards, for example, Bosch exclusively relies on specially authorized and qualified personnel for assembly and maintenance. “We also support our customers with documentation and instruction for users, and arrange for testing by certified experts,” explains Thomas Christian. A dense network of logistics centers and on-call services makes sure that security solutions reliably work as intended around the clock.