Greater security and efficiency by integrating intelligent functionality
Modern access management systems already fulfill several tasks today. With self-learning algorithms, new functions create further added value.
Functions
Increase security for people and values
Increase efficiency in processes
Easy integration into existing systems
Companies bustle with traffic day in and day out: employees, suppliers and visitors constantly come and go. Access management systems regulate who may enter where, when and how. To accomplish this, company passes or key fobs contain tiny chips that use radio signals to receive and transmit data. So that a company can flexibly control access to its facilities, all buildings are equipped with appropriate equipment. Depending on how a staff or visitor pass is authorized, doors either open or remain shut.
Today’s systems can also be designed and/or programmed to perform multiple tasks, ranging from access control across arming and disarming an intrusion system, to clocking hours worked. Instead of entering data more than once or separately administering various solutions, this results in a secure networked overall system that can be efficiently operated and used.
Networked access control and intrusion systems are already able to detect unauthorized entry or misuse. And when this overall system is combined with an intelligent self-learning algorithm that detects and reports deviations (anomalies) from previously learned normal values in how passes are used, it acquires new functions. Anomalies are unusual states that can reveal misuse or an intruder.
Protecting people and assets by intelligent solutions
In addition to improving security for the company and its property, intelligent analysis functions of this kind can also protect individual pass owners. To illustrate how this can work, let’s take the case of an employee who loses his company pass. He may not notice the loss right away and therefore can’t immediately report it to the security staff either.
A person who finds a lost company pass can theoretically take advantage of it to commit misdeeds. Perhaps to commit a theft? But if they enter a building at a time that is not typical of the pass’s actual owner, or take a different route or enter rooms that the owner doesn’t normally use, the intelligent system notices these deviations and alerts the security staff, who can then take action to track down and apprehend the wrongdoer.
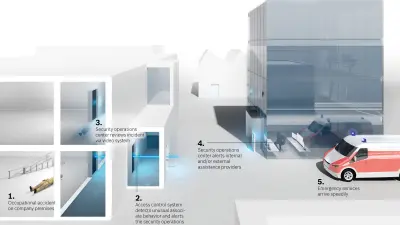
Say, for example, that an employee takes a walk on the company extensive grounds during a break. She trips and falls in an area that she normally doesn’t enter, striking her head and losing consciousness. The system detects this unusual behavior and immediately informs the security desk of a possible accident. The personnel can then use a video surveillance system to assess the situation, rush to provide assistance and notify the emergency medical service. The employee quickly receives help as a result, and the work of the security staff is facilitated.
Algorithm detects atypical behavior
Abnormal movement patterns of employees can also be detected (naturally without violating data privacy rules). For example, if an employee is present in a room unusually late, long after they normally go home. Could he be copying data without permission? The algorithm detects this atypical behavior and alerts the security force, which sends an officer to check out the situation and ask the employee what he is up to.
Of course, in order for this kind of analysis to work the system must be able to autonomously learn what the usual behavioral patterns are, on the basis of captured data. The first phase of implementation therefore consists of evaluating historical data from the access control system and calculating or describing normal values or conduct.
This naturally poses challenges. If a normal value is set too low, harmless activities will be reported as abnormal. If an excessively high value is chosen, many abnormal activities will be overlooked. The system deals with this by automatically learning and calibrating normal values during a learn-in phase.
For this purpose, activities are tracked and recorded during a defined time period. Then situation-dependent or -independent averages are calculated and subsequently applied as normal values. Their development is continually monitored so that the defined normal values and behavior can be adjusted at regular intervals. The system can also be tweaked based on specific requirements of the company.
Data privacy has top priority
When using anomaly detection methods like those just described, it is also essential to comply with data privacy rules, since the analyses are always based on personal data. All of the stipulations of the European General Data Protection Regulation (GDPR) must be obeyed. In many environments, personal data may not be stored at all or only briefly for certain purposes. The system available from Bosch permits both automatic anonymization and automatic deletion of personal data after the permitted and agreed storage period has elapsed. It is also possible to define role-dependent access to data.
The Bosch application runs securely on a separate workstation that is shielded from the company’s other IT infrastructure. Access to data stored on this workstation is governed by the four eyes principle, meaning that it must be approved by at least two people.
These security precautions meet the requirements of the GDPR and reliably prevent misuse of data by individual workers. This approach also ensures that the application complies with justified restrictions defined by a works council or a company’s own compliance guidelines.
Easy integration into existing systems
Open interfaces enable straightforward integration of the software-based solution in existing access management systems. There is no need to purchase and install any expensive new hardware components. Which intelligent analysis functions make sense depends on a company’s own data protection goals and requirements.
We advise and support you for mastering all of your challenges and implement the best possible solution from a single source.


